
Protocol: Malware Neutralization
Malicious code can compromise your entire operation. Learn the standard procedure for safe and effective removal.
Read Dossier →
Unwavering commitment to precision and success on every assignment.

Over 35 years of combined experience from our vetted and trained operatives.

Clear, upfront cost structures. No hidden variables. The mission is the priority.

Efficient and timely solutions that respect the critical nature of your operations.
Technical solutions for residential, commercial, and enterprise-level assignments.

On-site intervention for compromised PCs, laptops, and personal communication devices. We restore functionality with precision.

Upgrade your environment with secure, state-of-the-art automation. We handle installation and network integration.

One-on-one training sessions to enhance your operational capabilities with new hardware and software.

Proactive, continuous oversight of your entire IT infrastructure, from help desk support to co-managed deployment with your internal team.

Defend your digital assets. We deploy comprehensive security protocols, monitor for threats, and neutralize vulnerabilities.

Ensure operational continuity with secure, automated data backups and rapid restoration. We manage cloud migration, optimization, and security.
An opportunity to build your own enterprise under the Nerd Department banner. We are seeking qualified directors to lead new territorial operations.
Deploy with immediate recognition. Our brand is a symbol of trust, professionalism, and technical superiority.
Execute a successful business model refined for maximum efficiency, profitability, and client satisfaction.
Acquire clients effectively with our potent marketing strategies, materials, and national support network.
Receive comprehensive training at our headquarters, followed by continuous operational support from our veteran directors.
We are looking for leaders with strong management skills, a passion for technology, and a drive to build a successful business. Technical expertise is a plus, but a commitment to our operational standards is paramount.
Submit your preliminary application to receive the complete franchise disclosure document.
Declassified testimonials from satisfied clients.
Our strength is our personnel. We are actively recruiting the next generation of elite technical agents.
Make a tangible impact by solving complex technology challenges for businesses and individuals.
Stay on the cutting edge with access to new technologies, advanced training, and certification programs.
As our network expands, opportunities for leadership and specialization become available to our top operatives.
Forward your credentials and a letter of intent to our recruitment division.
Submit ApplicationInsights and intelligence from our top field agents.

Malicious code can compromise your entire operation. Learn the standard procedure for safe and effective removal.
Read Dossier →
Catastrophic data loss is not an option. A review of optimal backup and recovery protocols for all operatives.
Read Dossier →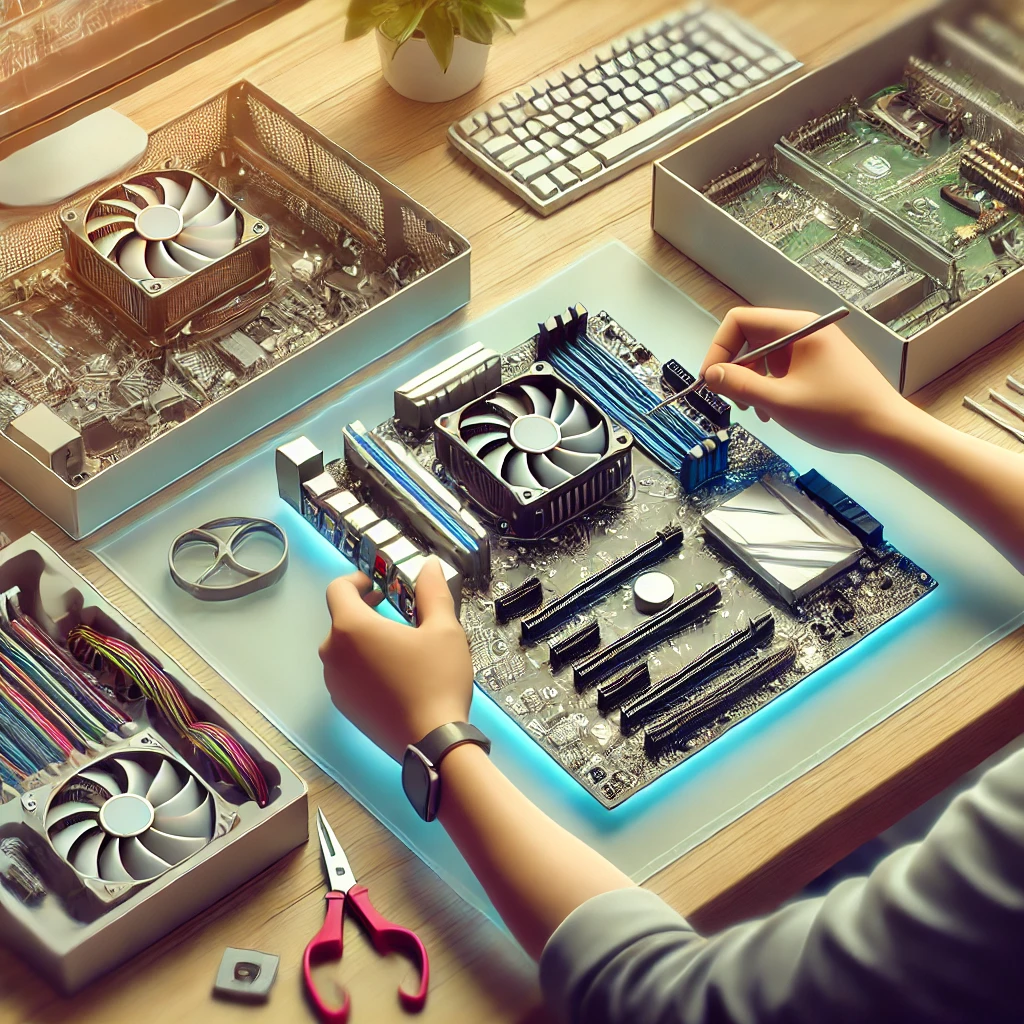
A step-by-step guide to assembling a high-performance machine for gaming, analysis, or field operations.
Read Dossier →Submit a service request, and a field agent will be assigned to your case immediately. Please be precise in your communication.